10 Steps To Developing a Secure Fintech App

How to expose personal information of nearly 150 million people in a single day?
Ask Equifax – a company responsible for one of the biggest data breaches of the century.
In just a few days the data breach cost them nearly $4 billion dollars! This was a far greater loss than investing in security measures from the start.
This has proven to be true as the company budgeted $200 million for security and technology last year.
According to a report done by Jupiter Research, the number of mobile banking users is expected to grow to 2B by 2020. This number will grow even higher, as more and more customers want to save their financial information on smartphones for easier use and future purchases.
Another study, conducted by the Clearing House in 2018, polled 1,500 people and found that two-thirds were extremely worried about their data and privacy while using fintech apps.
Fintech apps carry a lot of privacy risks and that is why most people feel uncomfortable sharing their financial and private information.
If you want your app to be used by as many people as possible, you need to highlight how safe it is beside the benefits it provides to users.
Below we list some of the latest data breaches in the fintech world along with the steps to make your fintech app as secure as possible.
Recent Events And Data Breaches
One thing is sure – consumers expect the highest level of privacy from banks and other financial services companies.
These companies possess a wealth of information about their customers, including personally identifiable information (PII), phone numbers, credit scores, addresses, social security numbers, credit card numbers, birthdates and more.
In the case of a data breach, hackers can use this information to steal money, create new bank accounts, open credit card accounts, file for tax returns, etc.
Data breaches have affected various financial service providers including banks, loan providers, payment processing companies, and credit reporting bureaus.
Here are just a few breaches that happened in recent years:
2005 – Card Systems Solutions – 40 million credit card accounts
2009 – CheckFree Corp. – 5 million people affected
2010 – Educational Credit Management Corp. – 3.3 million people affected
2014 – Heartland Payment Systems – 130 million customers
2017 – Equifax – 143 million accounts in the US
2019 – Earl Enterprises – two million credit cards
As these experiences show, security has to be the top priority for every fintech company.
They have a huge responsibility to properly safeguard people’s data.
After all, their whole reputation and existence will also depend on this.
Here are the important steps for making a secure fintech app.
1. Security Starts With the App Logic
If you’re going to build a fintech app, integrating security in each step of the app usage process is of utmost importance. A lot of omissions happen in this first crucial step.
A security policy for all participants in the project ensures a safe environment.
You will need to determine the most sensitive data you will deal with and how you’re going to protect it.
Here are a couple of tips for integrating the security in each step of your app usage process:
Only Store Crucial Information.
For example, keeping debit and credit card numbers for payments is usually not necessary. Some servers will only hold the token that identifies the billing method. The token is then passed to the system which will charge the customer. The server that requests the payment doesn’t have to know the billing information. This prevents the breach of payments database.
No one can steal sensitive information that isn’t there.
Apple Pay tried to limit the risk of major data breaches by popularizing this concept of tokenization – creating one-time codes for payments.
FinTech companies should have this in mind when looking for the right solution. Here are the best practices around PCI tokenization.
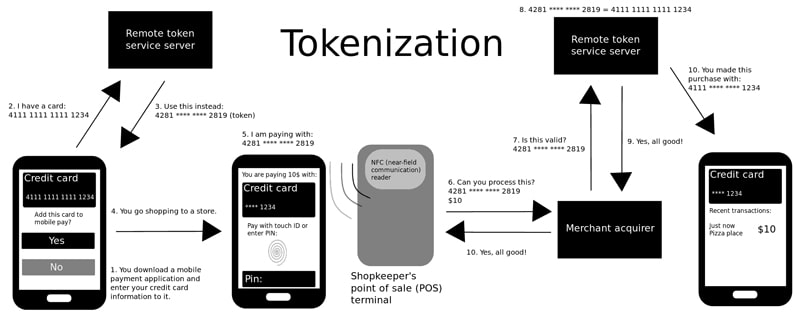
Source: Wikimedia Foundation
Think About the Roles and Permissions Structure.
Your app is going to have features that not all users are allowed to access. Since fintech apps are quite complex, you are going to need a system for organizing permissions and setting up roles. RBAC (Role Based Access Control) is a system that can help you do just that. It is quite easy to implement as it works in the way the administrators think. An alternative model is ACL (Access Control List) which lists all the operations a particular user can do.
Force the Use of Complex Passwords.
Any company that deals with money transactions need to have a strong authentication plan in place. A username and password are basic credentials and they can easily get stolen or hacked. FinTech companies can force the use of complex passwords and make their users change the password every 2-3 months.
Enforce the passwords with an extensive character set. They should also have at least 14 characters in length.
2-Factor Authentication.
This is a great method for improving your app’s security and going beyond the basic authentication method that consists of having a username and a password. One of the most common methods for 2FA is the use of a one-time code via SMS or email. Another popular method is a push notification that allows users to authenticate themselves with a single touch.
Log Everything.
You should log any user activity from every user at all times. This may include, but is not limited to the following:
- the action (e.g.: transaction),
- User ID or account in the platform,
- IP address,
- geolocation,
- device data, and other important information.
These logs need to be easily accessible during a potential ‘post-mortem analysis’ when the incident has to be reviewed from all angles. Logs are vital for a proper incident post-mortem report that should include the complete timeline, root cause analysis, and incident details.
Monitor, Alert, Block.
You need to be able to monitor all transactions and freeze the ones that seem suspicious for later review. You can create your own fraud scoring methods or use them in conjunction with 3rd party solutions. Transactions can be rated as low, medium or high risk. In the case of a high-risk transaction, the system will decline the query and send the alert to the responsible employees who will inspect these log actions.
Integrate Multi-Step Approval Processes for Key Actions.
In case of some key actions (e.g. large transactions, edits in some crucial ) it makes sense to request approval from several participants before actually executing it. Apps may integrate sequential or parallel approvements, depending on the business process, similar policies help to reduce risks of mistakes or successful attacks.
2. Write Secure Code
Secure code is one of the most important components of the fintech app.
Important personal data will be saved on the user’s device and secured on the server. This is why it’s so crucial to create proper algorithms as that will help you easily find any flaws in the code.
Scan the source code often and test it for any vulnerabilities.

Make sure the code is agile and easily portable between different devices and operating systems. This allows software engineers to quickly act and update code in case a data breach of any kind happens.
Here are some recommended practices when it comes to securing your app’s code:
- Include Input Validation
This is one of the most important security steps for developers.
Input validation will prevent hackers from injecting your app with malicious code, by either sanitizing or rejecting the input.
Unfortunately, the lack of input validation is the reason why so many websites and apps get hacked.
- Check The Data Sent To External Networks
If some sort of data is sent to external networks make sure it is only the absolute necessity. Review the data often to make sure that no sensitive information is being sent.
- Deny by default
The best way to secure your app is to deny access to all apps functions. Only allow it on a need to need basis when something has to be accessed.
- Check for framework messages
Most tools developers use have security mechanisms in place. They can automatically check for any flaws in code so be sure to pay attention to these warnings.
- Prevent broken access control
Defining access control rules is strongly recommended when building a secure fintech app. This area should include insecure IDs, file permissions and client-side caching. A failure to implement an access control policy can lead to disclosure and unauthorized use of data.
- Protect against SQL injection
An SQL injection is still an effective hacking method. One of the best ways to test the vulnerability of a fintech app is to conduct your own attacks on the app and see whether they were successful or not. It’s also vital to apply patches and updates as soon as possible.
- Prevent Sensitive Data Exposure
The first step is determining which data is the most sensitive. That will require additional protection that can be implemented in a couple of ways. Some of the most common measures are installing an SSL certificate on the site, never transmitting data in clear text, and using a web application firewall.
OWASP is one of the best resources on anything related to web security. They publish articles and documentation on this field.
3. Infrastructural Security
Ensuring the best possible infrastructural security is a must for any fintech app.
Here are the best ways you can achieve that:
Implement Perimeter Defense.
This layer is related to proxy servers and firewalls. Make sure that routers are properly configured because that will protect against internal attacks.
Maintain Operating Systems and Application Servers on a Regular Basis.
Operating systems are another important foundation of infrastructural security. This layer can be improved by updating all system updates on a consistent basis. Tools like Microsoft’s Software Update Service and RedHat’s up2date service can help with the automation of your operating system.
Do Not Install Apps or Services on the Server.
Unless that’s absolutely necessary! For example, utilities, office tools, email clients, etc. should not be on the server. It’s always best to keep the policy of ‘required minimum’ (open ports, running services, etc.)
Manage Third-Party Components.
The process of managing third-party components needs to begin as early as possible. If a third-party component is incorporated in a product it needs to be monitored on a continuous basis. Third-party components caused a lot of risk in recent years – Heartbleed bug is one of the best-known. This includes maintenance and updates to the latest stable version, monitoring, and alerts for found vulnerabilities, and policy for action in case a vulnerability is found in a dependency.
Have Failover Redundant Infrastructure.
Lately, a lot of businesses started utilizing the AWS cloud as a way to enable faster disaster recovery. This solution can also help you minimize the impact of DDoS attacks on your fintech application.
In order to minimize downtime and service interruptions, you should implement high availability for your infrastructure.
Systems that are highly available are able to recover from server or component failure automatically.
Each layer of your technology stack should be prepared for redundancy.
High availability will depend on several factors:
- environment
- hardware
- software
- data
- network
Each of these components needs to be able to handle unexpected failures.
Creating a high availability setup will require load balancers which are an essential piece of software at the application level.
The most common choice for load balancing is HAProxy (High Availability Proxy) because it can handle load balancing for different serves and different layers.
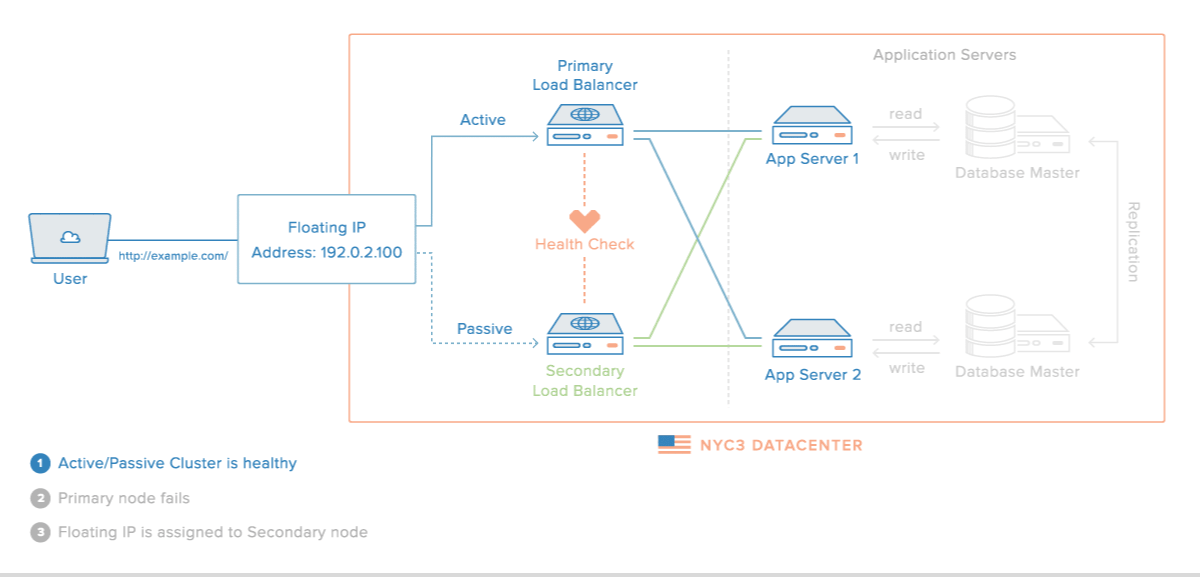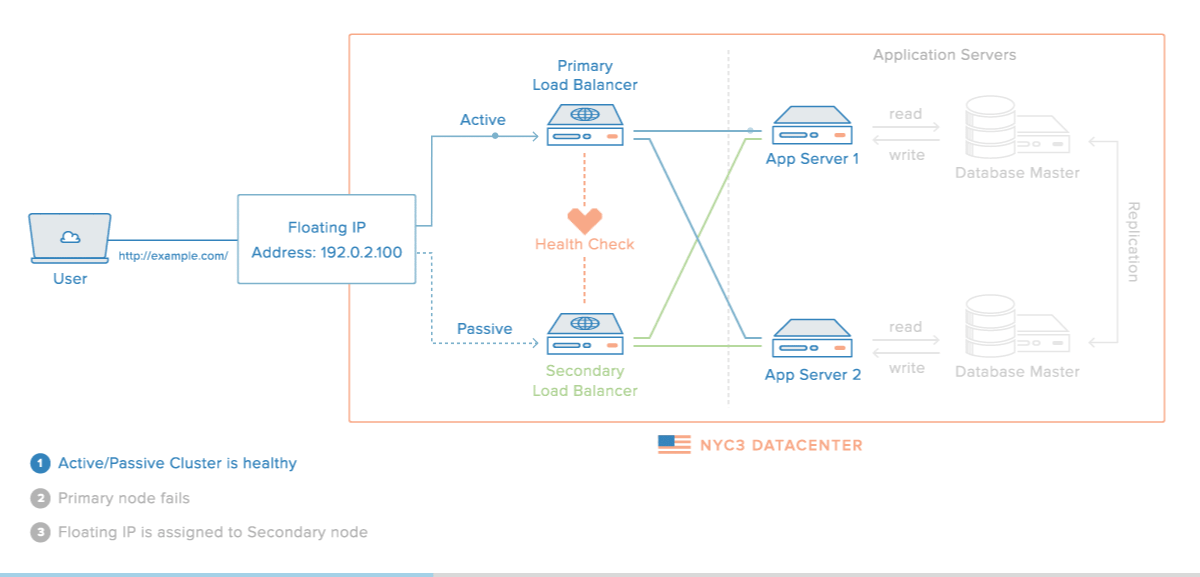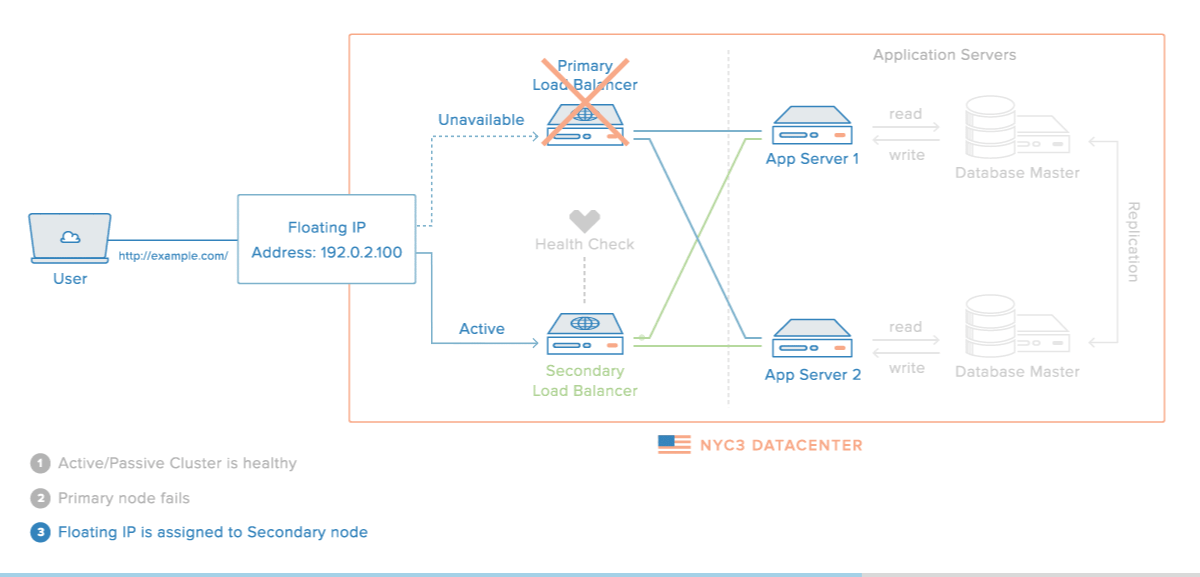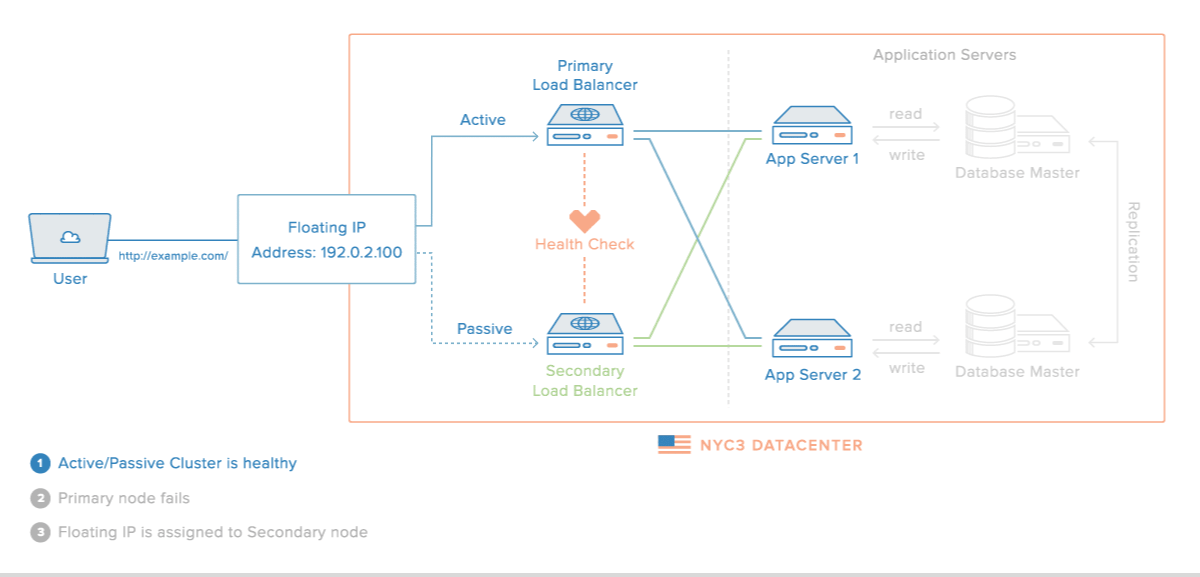
Source: Digital Ocean
Protect Web Server.
As web servers (or application servers) are the main outside world facing units, they are one of the most targeted aspects of any business. Web files should always be located on a separate drive than the operating system, logs, and other system files.
You can also implement a Content Security Policy (CSP) which is an added security layer that prevents certain types of attacks such as Cross-Site Scripting (XXS) and data injection.
Using signed cookies is a good option when you want to restrict access to your content without changing its URL.
Use HTTPS.
Google recommends the use of an HTTPS SSL certificate as it keeps your user’s data safe and secure. Modern browsers alert users if the website or web app they use isn’t currently using a secure SSL connection – so for modern apps, it is a de-facto standard to force SSL for any request they serve.
Use a VPN Layer.
VPN, as defined by its name, allows building a secure network using public internet lines – which provides the possibility of e.g. granting access to certain services, pages, or other components of the app only from hardware that provides a valid public key. The initial setup can be a little bit complicated but the improved security is worth it for most cases.
Do Regular Maintenance.
Falling back on website security and maintenance can greatly impact the security of your fintech app. You can hire a dedicated DevOps specialist who will do a regular check of the system and its components.
4. Integrate Security in Your Day-To-Day Workflows
According to Kaspersky, almost 52 percent of businesses admit that their employees are their biggest weakness when it comes to IT security.
The human factor can greatly impact the company’s security. System misconfiguration, lost devices, clicking on an unsafe URL are just some of the ways that employees compromise their organization’s security.
In case anything goes wrong, here are some solutions that can provide quick and easy recovery:
Have a Backup Policy in Place
An automatic backup of code, all files and databases is extremely important. The frequency should be determined during important organizational meetings. In the beginning, you should conduct backups every three months. It’s best to pick an independent backup program that will let you choose which data should be stored and how often.
Here, at TMS Outsource our backup practice is the following:
- every day for the last 90 days
- every Monday for the previous year
- every month for the previous three years
The backup program should have a user-friendly interface for quick access and easier recovery so you don’t waste any additional time ($$$).
Exercise the Disaster Recovery Rehearsal
Companies that operate in the fintech space simply need to have this policy as an integral part of their strategy. It means that a company will simulate an attack and perform recovery, and will then review its disaster recovery process and some key metrics (downtime, potentially lost data, breaches) in the search for any flaws and security issues. These live simulations should be done at least once a year.
Separate Development, Pre-Production, and Production Environment.
To reduce the risk of production data going into the wrong hands, you should separate development, pre-production, and production environment. This means that developers only have access to the development stage, without any production business-critical data, while higher management is involved with the pre-production and production stage.
Use Corporate Hardware
When accessing any back-office or development-related interface, make sure to only use corporate hardware.
Have Non-Disclosure Agreements in Place
A non-disclosure agreement is a very important document in the fintech app development process. You should sign an NDA with your employees, independent contractors and anyone else who will have access to important information on the fintech app.
Implement ISO 27001 Certificate
This is one of the best certification standards for information security. Many banks require the implementation of ISO 27001 certificate by FinTech organizations. The certificate covers areas such as security policy, risk assessment, incident management, and more.
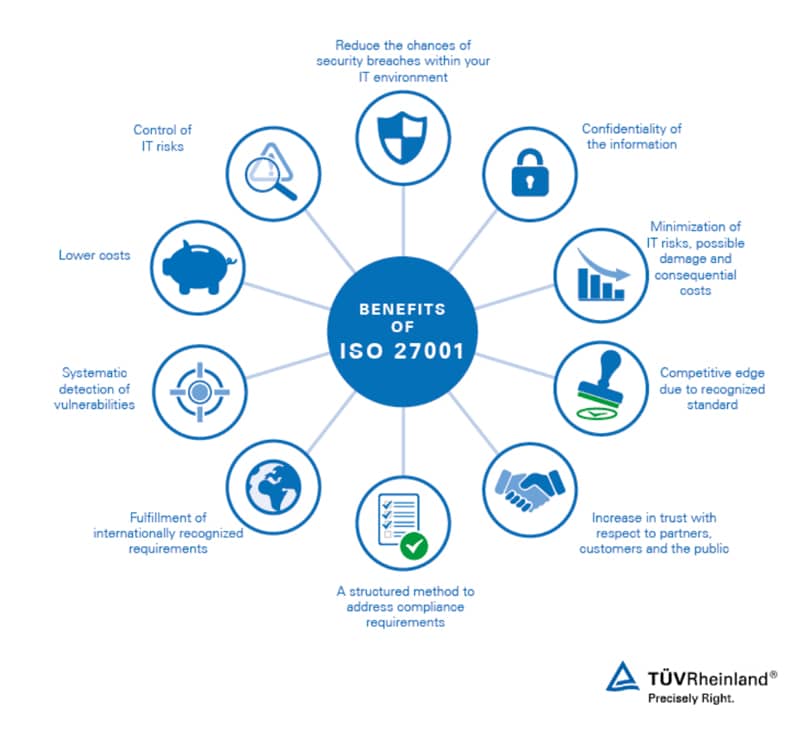
Source: TUV.com
5. Include the Testing Stages
Testing is an integral part of every software development process. Fintech apps are specific because they need to be constantly tested for security.
While you’re working on developing a fintech app there are a couple of testing stages that need to be included in the process:
- Check Network Security
The first thing that should be tested is your network – servers, network devices, and DNS.
The most critical areas are the ones that are easily exposed to the public. That’s why the focus should be on servers, routers, and firewalls first.
Also, check your operating system, the database, storage, and other components that are at risk of being compromised.
Your system should have all the latest security patches installed.
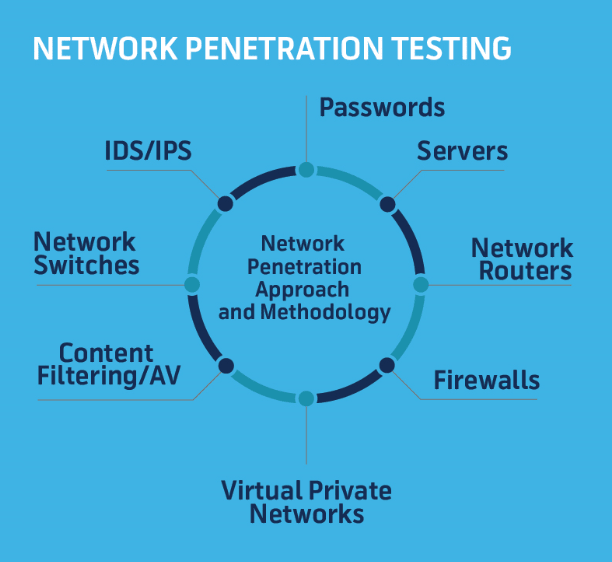
Source: Red Team Secure
- Check Everything From The Client-Side
Client-side penetration is also known as internal testing. It consists of checking the application while it’s running in the browser and making sure that no breach can occur.
This specific test can answer a couple of very important questions such as:
- Are there any vulnerabilities?
- If yes, what harm can be done?
- Are the access rights for employees set correctly?
- Can we detect any weak points?
This process consists of JavaScript execution, HTML injection, CSS injection, Clickjacking, and testing local storage.
- Server Security Testing
When it comes to the server-side of security testing, you need to make sure that the proper frameworks and tools are in place. Initially, security tests should be done in-house. However, the best practice is to have an external audit done at least once a year. Hiring an independent security firm to do a yearly penetration test is often a requirement by some enterprise clients. That’s because penetration testing is one of the most widely used techniques to comply with various regulations.
6. Have a Solid API Security Strategy
Mobile apps use APIs to interact with back-end information. API keys and tokens have a crucial role in the app’s security and efficiency. One of the best practices for protecting an API is to implement an automatic API token rotation. The easiest option is to implement the OAuth 2.0 standard.
- API tokens should be regularly rotated
APIs are also responsible for the functionality, content, and data so ensuring proper API security is another important aspect of creating a secure fintech app.
API security stack should consist of three important security measures – identification, authentication, and authorization.
7. Have an Identification, Authentication & Authorization System Ready
Your identification, authentication, and authorization system need to function flawlessly.
In the information world, identification is analogous to entering a username or a name. Your user is claiming to be someone.
Authentication is how a user will prove that they are who they are. This is usually done via a password as one of the verifying methods.
The password is just one authentication method. For example, you could also use an RSA token or a smart card. In recent years, bio-based authentication has become more common. Users can now verify their identity via a thumbprint or a retina scan.
If you want to improve the safety of your users and add one more layer of security, you can also add two-factor authentication.
Authorization is the last step. After someone was both identified and authenticated, the next step is to determine what this person is authorized to do.
The API should restrict access to all important areas. Your users can only get authorization for completing specific tasks and issuing certain commands. Some common authorization types also include route assignments, bandwidth traffic management, IP filtering, etc.
8. Use Data Encryption
Encryption protects data sent to different entities. This is a vulnerable moment when data could be stolen. That’s the reason why it’s one of the hardest parts of securing data.
Encryption sends the original form to the right user and meaningless data to hackers and unauthorized users.
There are various data encryption algorithms that can be used.
AES (Advanced Encryption Standard) is considered to be the safest one. It is also used by the US Federal Government. Almost all Android and iOS applications run this encryption method.
Other industry-tested algorithms include RSA (2048 bits and higher), TDES (minimum double-length keys), ECC (160 bits and higher).
Having HTTPS or SSL during transmission is not enough. All of your databases need to be protected by data encryption.
The Federal Financial Institutions Examination Council stated that financial institutions and banks should encrypt information such as:
- Personal information that a user gives to get a specific service or a product (for example – name, address, income, social security number)
- Any information that can be received from a transaction (for example – payment history, credit card purchases, account numbers)
- Information that can be received in connection with providing specific financial service (for example – a consumer report)
9. Educate Customers
You should also educate your users on some basic security tips. They are also responsible for protecting their data and they should be very proactive about it.
Below, we list a couple of things you should pay attention to:
- Use authorized app stores only because they make you less prone to cybersecurity attacks
- Never store the username and password in the fintech app
- Don’t use the app on a public WiFi network
- Rooting your device can make you more vulnerable to hackers
- If your organization has a BYOD (Bring Your Own Device) policy be extra cautious
- Use VPN as an added security measure
- Use an anti-virus software
Many customers are not aware of how a fintech app will collect, store, and use their data. Keep your customers educated by offering a document easily accessible from your company’s website with best practices and detailed tips.
10. Use Payment Blocking
Your fintech app could use a payment blocking feature. This mechanism can block unusual activity such as withdrawing from an unusual place or withdrawing an unusual amount.
These measures are used by many banks and financial services in order to prevent theft of their customers’ money and data.
Outsourcing Fintech App Development – Yes or No?
Many companies decide to outsource the development of their fintech app because it is more cost-efficient.
They don’t have to hire full-time employees or invest in overhead. Mobile app development companies also have a lot of experience in the IT industry. That reduces the risk an employer would carry if they were to hire a new person.
If you’re looking to outsource the development of your fintech app there are a couple of things to take into consideration.
Is the Company Expert in Fintech Field?
If you have decided to seek an outside partner to help build your fintech app, make sure they are experts in the fintech field. They should be very knowledgeable about different aspects that are needed in order to build a secure fintech app. Ask a lot of questions about the developer’s experience in the fintech space.
Are They Security Experts?
Sure, your developer has to be super experienced at writing code. However, in the fintech space, being knowledgeable about data and security is necessary. It is simply a prerequisite for being an expert in fintech technology.
Is There a Diverse Skill Set?
Startups usually look to hire one developer for their project. One developer could probably pull off the whole project but there are a few downsides to this option.
Building a secure fintech app requires a diversified skill set and that is why hiring a company with a team of developers is a better option.
The knowledge of more than one programming language is often required and expertise in graphics, layout, and technical writing is also often required.
Check for Testimonials
One of the best ways to research prospective development company is to check for testimonials and case studies with the successes of their clients.
If you decide to work with just one developer, be sure to ask for their digital footprint. Check their website and the complete list of services they provide.
The Problems Fintech Apps Will Continue To Face in the Future
Although fintech is considered the future of finance, this industry still faces a lot of problems.
The regulatory bodies usually have two different approaches to the fintech industry and services.
One is quite passive where regulatory bodies don’t really stand in the way of fintech companies, but they don’t want to help them either.
The other one is restrictive and is loaded with roadblocks and bureaucracy. For a fintech company, that makes it quite difficult to survive on the market.
Data and privacy will also continue to be one of the main issues associated with fintech apps. Fintech companies will have to be transparent with their security practices and they will need to ensure the highest level of privacy for their users. If you are interested in reading more, check the future fintech features a successful mobile app must have.
…
At TMS Outsource we are driven by building top-notch mobile apps. We would love to help you build yours so schedule a free consultation and tell us about your idea.
